As discussed in previous posts, the most common entry point into networks is Phishing/Smishing/Vishing. The malicious actor is trying to access your network and data through your employees. However, knowing this tactic and knowing what to do about it are two entirely different things. We will use real examples to illustrate the critical information employees need to remain educated so their ASC can avoid becoming the next victim.
Phishing/Smishing/Vishing attacks use what is called Social Engineering. Social Engineering is used to persuade the end user to act on behalf of the malicious actor and, unfortunately, is a widespread approach because it is so successful. Even trained professionals have fallen prey to well-honed social engineering attacks when distracted or rushed. Whether via email (phish), SMS text message (smish), or voicemail (vish) containing a threat of bad things or a request from “management,” the net results can be potentially devastating to the organization and its patients.
As a recipient of a message, there are some essential questions you should ask yourself before opening an email, clicking on a link inside an email or SMS message, or opening an attachment embedded in an email.
- Was the message expected?
- Am I asked to do something the sender has never asked the recipient to do before?
- Does the message indicate a sense of urgency?
- Is there a claim that my organization or I will be penalized if we do not act immediately?
Here are some examples and red flags to look out for from actual phish emails, SMISH SMS messages, and VISH scams I have seen used.
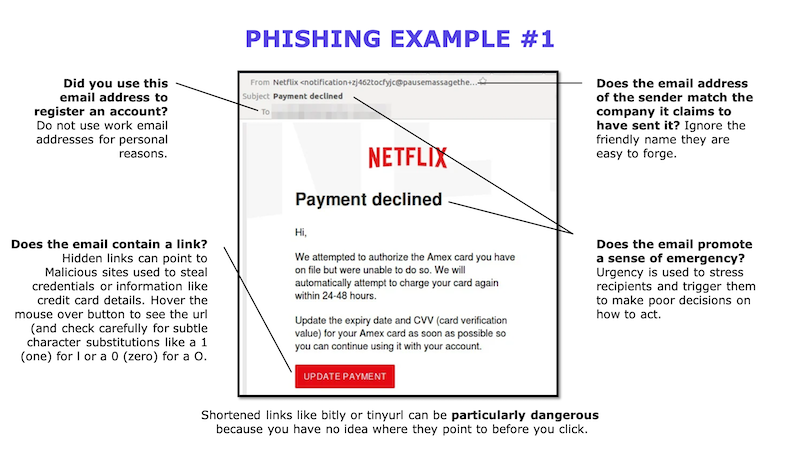
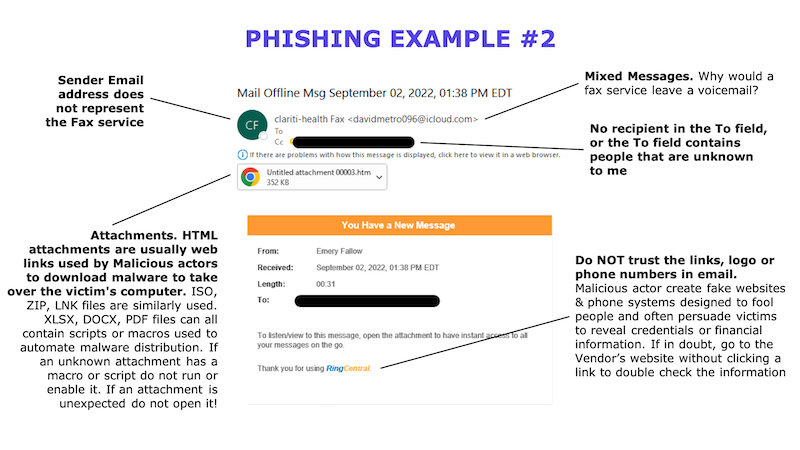
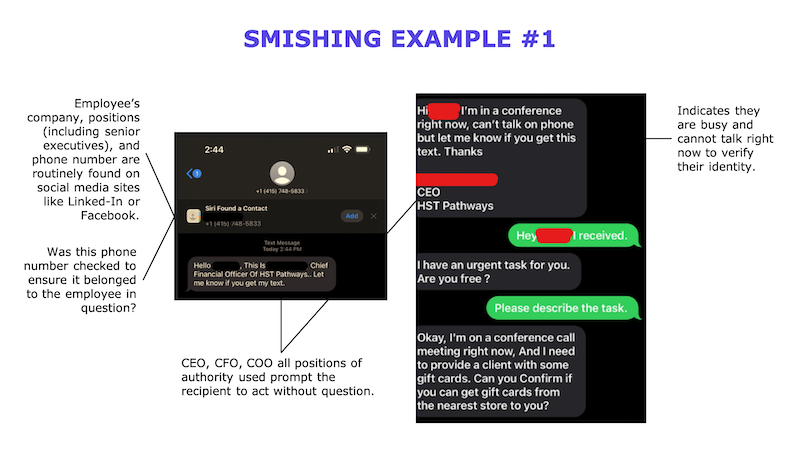
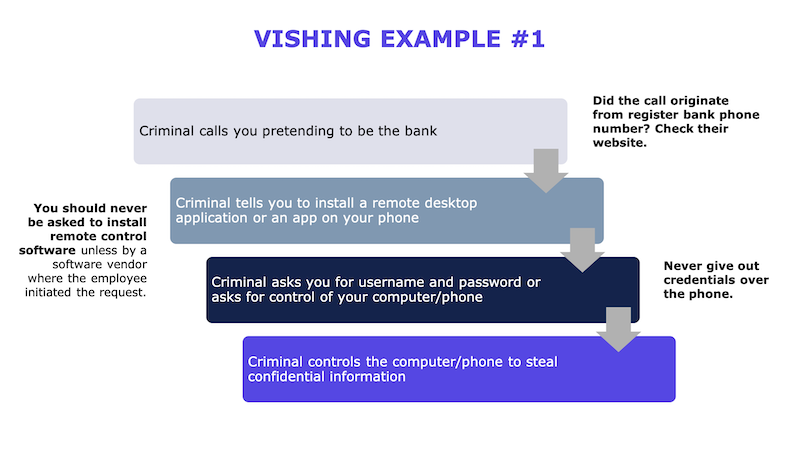
What can my ASC do to help protect our patient’s data?
Repetitive employee training is the key to success, as malicious actors’ tactics constantly evolve. A one-time training event will not improve your ASC’s security posture. People forget, become complacent, or are too busy to pay attention.
Many security awareness vendors can provide easy-to-digest training to ASC employees. This training needs to be reinforced with regular automated Phish tests. The Phish tests are safe and pretend phishing emails that exhibit many red flags of an actual phishing email without the danger of malware distribution or credential theft. It’s better to learn the warning signs from failing a test than by suffering a breach of your patient’s confidential information.
A good reference for phishing email red flags can be found below. Since we are trained not to click on links, you can copy the address below into a web browser address bar.
www.knowbe4.com/hubfs/Social-Engineering-Red-Flags.pdf
Stay Vigilant.
Don’t miss out on the good stuff – Subscribe to HST’s Blog & Podcast!
Every month we’ll email you our newest podcast episodes and articles. No fluff – just helpful content delivered right to your inbox.

