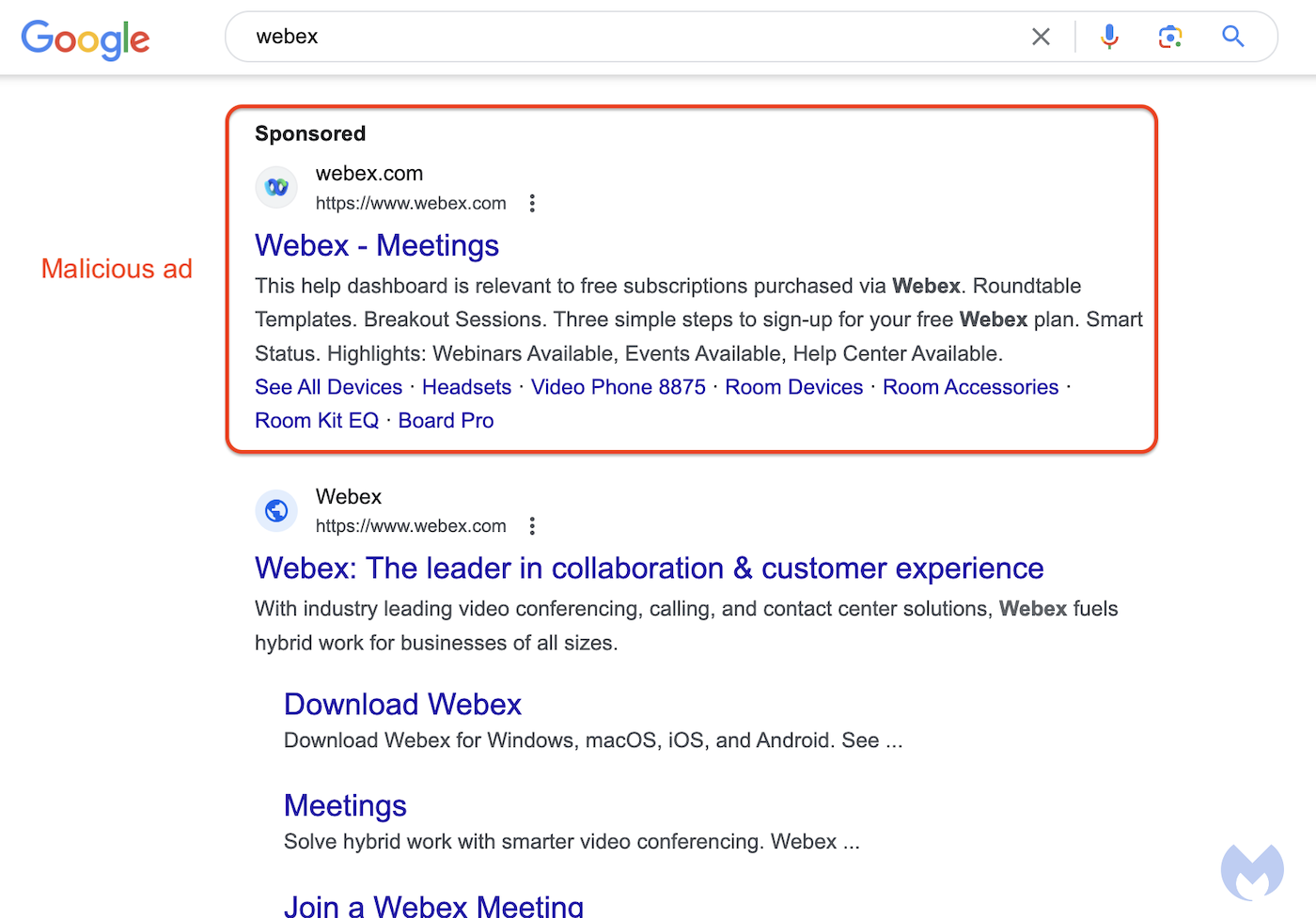
What is Malvertising?
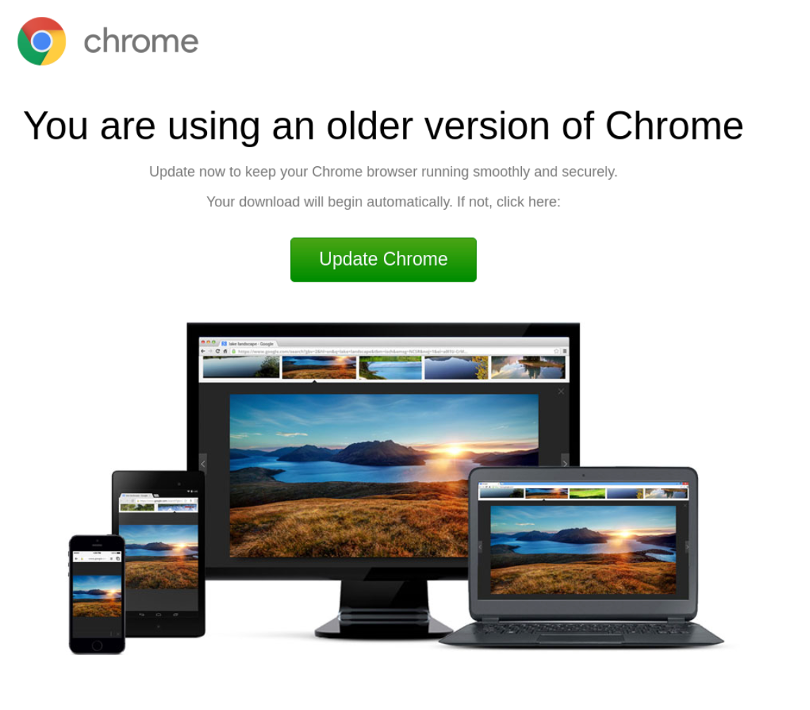
Malvertising is sometimes referred to by the less catchy term SEO Poisoning (Search Engine Optimization). Malicious actors have worked out how to create fake websites that copy legitimate company sites and then create ads in popular search engines (Google, Bing, etc.) that typically appear higher in a search listing than the legitimate website. Clicking on these ads will direct the unwary user to the fake site or, more concerning, a legitimate site that has been compromised (e.g., software sites for well-known applications that require you to download something). The software available for download has been booby-trapped, so if installed, the device is compromised by malware. Another variation of this approach is to present the user with a page stating that a “browser update is required before the user can continue to the site.” Unsurprisingly, the browser update is malware used to take control of the device or steal the user’s credentials. Some malicious actors have even worked out ways for the displayed link in the ad to look identical to the real thing! With a malicious ad, by hovering over the hyperlink, you will see it points somewhere else. Search engines are trying to combat this, but it is a race between the bad actors and the companies whose business model depends on ad revenue.
What should employees at an ASC do?
Avoid clicking ad/sponsored links. If possible, use a verified URL directly to a website (preferably from a favorites list).
What is AiTM?
AiTM (Adversary in the Middle) is a sophisticated attack. It usually starts when a person receives a phishing email. For example, it could be from the “IT Team” or “DocuSign” or another compromised employee or customer. These emails will contain links, booby-trapped attachments, or QR codes (see QSHING below) that look like they point to a legitimate site. Or if the target site has already been compromised, they might look completely legitimate.
In either case, the user is typically prompted for credentials and, if applicable, MFA codes. This information is relayed to the actual identity provider to allay suspicion, but not before the credentials are stolen. Even worse, the authentication token issued by the identity provider is intercepted. This allows the malicious actor to impersonate the victim for some time without needing access to the MFA device. It allows, in effect, complete account takeover, and the thief can maintain access to the stolen account undetected. The malicious actor can impersonate the affected user or ASC employee to steal data/money or distribute malicious links to other employees/customers who assume they come from a trusted source.
What should an ASC employee do?
Be very wary of links in emails or QR codes. Contact the sender (not by email) to confirm the legitimacy if the email is unexpected. As a general rule, do not click links! If possible, go directly to a website using a verified URL (preferably from a favorites list). Be very careful if you are unexpectedly prompted for credentials or requested to install an “update.” Do not install/provide credentials; close the window and ask your IT team for advice.
What is QShing?

Malicious websites can then direct the user to install software (usually malicious), a fake browser update (typically malicious), steal data (to be used for extortion), or steal credentials.
What should an ASC employee do?
The difficulty is that there is no way for a human to look at a QR code and know whether it is legitimate and safe or malicious. The safest option is to educate your fellow employees and families to only scan QR codes if you are 100% sure they are legitimate.
You can find additional helpful information regarding Phishing, Smishing, and Vishing here:
https://www.hstpathways.com/blog/the-most-common-indicators-of-a-phishing-smishing-vishing-attack/
Stay Vigilant.
Don’t miss out on the good stuff – Subscribe to HST’s Blog & Podcast!
Every month we’ll email you our newest podcast episodes and articles. No fluff – just helpful content delivered right to your inbox.
